Without encryption, plain text email messages can be easily intercepted and tampered with in-transit. Modern email servers, especially major webmail providers such as Gmail or Outlook.com, do typically exchange emails over SSL/TLS connections, reducing the likelihood of tampering, but this does not equate to zero-knowledge, end-to-end encryption. An email provider could be compelled by the authorities to decrypt and hand over the messages, either during the transmission process or when they land in a users’ inbox.
Most, but not all MX servers support secure connections for incoming email messages. Without your own end-to-end encryption scheme however, it is trivial for an attacker to target emails sent to any mail exchangers that do not require a secure connection.
S/MIME Encryption vs PGP Encryption
There are two standards for end-to-end email encryption that are commonly used today. They are S/MIME encryption and PGP encryption. S/MIME is a more centralized standard which relies on a PKI (public key infrastructure) typically maintained by a user’s IT department (in the enterprise) or a commercial certificate authority. The PKI takes a certificate signing request, and issues a PKCS #12 certificate bundle consisting of a public and private key for the user. To sign and read encrypted emails, the user uses their private key – which is never shared. Others wishing to encrypt emails for the users’ eyes only must first obtain a copy of their public key. The user can facilitate the key exchange by simply sending a signed email to the party who they would like to correspond with.
PGP encryption is more decentralized standard which is popular with private users. A user can generate their own PGP keypair, consisting of a public and private key, without the involvement of a certificate authority. Some browser extensions or webmail clients, including Mailvelope and Afterlogic Webmail Lite PHP, provide the functionality of generating a PGP keypair right in a users’ browser. If the user prefers to generate their keys offline, they can use a desktop app such as OpenPGP or GnuPG. Once a keypair is generated, the user may upload their public key to a public key server such as the Mailvelope Key Server, so other PGP users can know that an email signed with that public key should be trusted as being authentic, and also send encrypted email to the user. If the sender and recipient do not use the same key server, then a key exchange (similar to S/MIME) must first take place by the two parties sending each other a copy of their respective public keys.
For more information about using zero-knowledge PGP encryption with Mailcow, read our article about integrating Mailcow with the Afterlogic webmail client, which supports the OpenPGP.js library used and maintained by ProtonMail.
The most popular desktop mail clients, including Microsoft Outlook and Mozilla Thunderbird, support S/MIME email signing and encryption out of the box. Using PGP requires a separate software which signs and encrypts the plain text email into ciphertext. The PGP encrypted message block is then copied and pasted into the sender’s email client.
Although popular hosted email services such as ProtonMail and Tutanota use the PGP encryption standard since they automatically facilitate the key exchange between users of the same service, this article covers how to use S/MIME encryption with any mail server, such as a Mailcow mail server which you host on your own. For simplicity without needing to set up an entire PKI for personal users, it relies on Actalis, a certificate authority based in Milan, Italy, to obtain a free S/MIME certificate valid for one year.
For enterprise use, it’s preferable to set up your own public key infrastructure which issues and distributes S/MIME certificates to your users, as it doesn’t require placing your trust in an outside certificate authority, in this case Actalis.
Note that neither S/MIME nor PGP encrypt the email headers, which include metadata such as the sender, recipient, and subject line of the message. Any private information should always be written in the body of the encrypted email, not the subject line – to keep it safe from prying eyes.
Obtain a free S/MIME certificate from Actalis.
Visit https://extrassl.actalis.it/portal/uapub/freemail?lang=en and type in the email address you wish to obtain a S/MIME certificate for, then click Send Verification Email. Momentarily, you should receive an email with the verification code in your inbox.
Copy and paste the verification code into the Verification code text box on the Actalis page. Complete the CAPTCHA then check the boxes to confirm you agree with the terms and conditions. Although you must acknowledge and accept the Privacy Information under the GDPR, it is not mandatory to consent to the use of your data for marketing purposes.
Finally, click Submit Request. You will proceed to the next page with the passphrase for your certificate. Save it in a safe place as it will only be displayed once. The certificate bundle (a .zip file containing a .pfx file) itself, without the passphrase, will be emailed to your inbox. In order to import the certificate into your keychain later, you will require both the passphrase and the certificate file.
End-to-End Email Encryption with PKCS #12 Certificates in Outlook and Mailcow
This article assumes that one is using Outlook 2016 for Mac, but a similar process can be followed using Outlook on Windows.
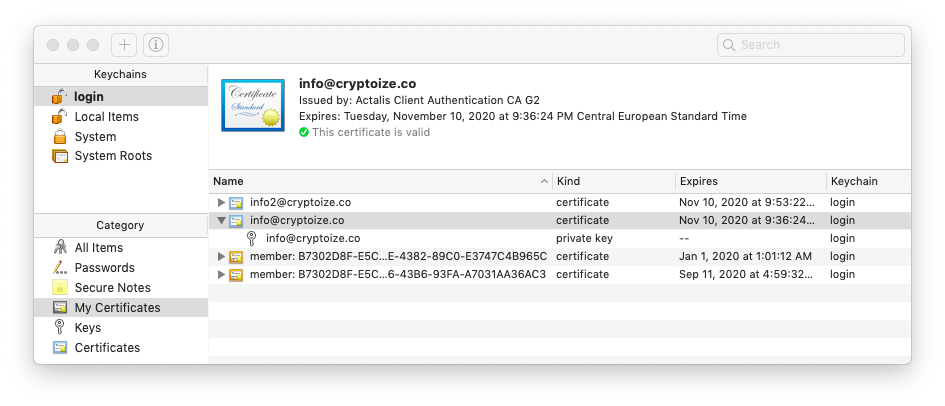
Ensure you have the .pfx certificate file and passphrase for your S/MIME certificate obtained from the previous section. Launch Keychain Access from your Mac desktop. Select the login keychain from the top-left pane, and the My Certificates category from the bottom-left pane. From the taskbar, select File > Import Items and browse to the .pfx certificate file. When prompted, enter the passphrase for the certificate then click OK. If importing the certificate was successful, you will see it listed in your keychain like this:
 Next, open Microsoft Outlook and select the inbox corresponding to the certificate. From the taskbar, select Outlook > Preferences then click Accounts in the Preferences window which pops up. Select the account corresponding to the certificate and click the Advanced button. Then, select Security, beside the Servers and Folders options. From the dropdown menus for Digital Signing and Encryption, select the certificate corresponding to the email address.
Next, open Microsoft Outlook and select the inbox corresponding to the certificate. From the taskbar, select Outlook > Preferences then click Accounts in the Preferences window which pops up. Select the account corresponding to the certificate and click the Advanced button. Then, select Security, beside the Servers and Folders options. From the dropdown menus for Digital Signing and Encryption, select the certificate corresponding to the email address.
In addition to the default options Send digitally signed messages as clear text and Include my certificates in signed messages, we recommend that you check Sign outgoing messages to digitally sign every outgoing email by default.
Selecting the checkbox for Encrypt outgoing messages might not be suitable in all cases, as you must have a recipient’s public key in your Outlook contacts list, before sending an encrypted email to them. If you try to encrypt an email message but don’t have the recipient’s public key yet, Outlook will pop up with a warning saying that there was a problem with the recipient’s public key, and ask whether you want to send the email as plain text.
Even if you don’t check Encrypt outgoing messages, you can still encrypt individual email messages (where you have the contact’s public key) by going to the Options tab of the New Message window, clicking the Security icon marked by an envelope and padlock, and selecting Encrypt Message.
End-to-End Email Encryption with PKCS #12 Certificates in Thunderbird and Mailcow
Adding a S/MIME email certificate to an account setup in Thunderbird is equally as easy as Outlook. Launch Mozilla Thunderbird from your desktop. From the taskbar, select Thunderbird > Preferences. In the preferences tab that appears in-line in the Thunderbird window, navigate to Advanced and select the Certificates tab, then click Manage Certificates.
In the Certificate Manager pop up window, select the Your Certificates tab, then click Import… and browse to the .pfx certificate file on your desktop. When prompted, enter the passphrase associated with the S/MIME certificate, then click OK.
If your certificate was successfully added, you should see it listed similar to this screenshot:
 Click OK then return to the primary Thunderbird tab showing your inbox and email messages. Right click (or two finger click) the email address corresponding to the S/MIME certificate which you just imported, then select Settings from the context menu.
Click OK then return to the primary Thunderbird tab showing your inbox and email messages. Right click (or two finger click) the email address corresponding to the S/MIME certificate which you just imported, then select Settings from the context menu.
Select Security from the pane on the left hand side. Then for Digital Signing and Encryption, click Select… to choose the correct certificate in your certificate store, matching the email address.
We recommend signing all email messages by default to distribute your public key to anybody who may want to correspond with you by encrypted email. To achieve this, select the Digitally sign messages (by default) checkbox.
As the default encryption setting when sending messages, it may be better to leave that as Never (do not use encryption) so you can still send messages to recipients who you don’t have the public key for yet.
 You can still encrypt messages individually from the Write window where you compose your emails in Thunderbird. Simply click the Security dropdown from the toolbar and check Encrypt This Message.
You can still encrypt messages individually from the Write window where you compose your emails in Thunderbird. Simply click the Security dropdown from the toolbar and check Encrypt This Message.
 The seal and padlock icons in the bottom right hand corner denote that the message will be digitally signed and encrypted.
The seal and padlock icons in the bottom right hand corner denote that the message will be digitally signed and encrypted.



