When most people think about the dark web, they think it’s a sketchy place where the ne’er-do-wells of the Internet gather. Despite its negative connotations to the less informed, the dark web made up of Tor hidden services has legitimate purposes. What is a Tor hidden service? It is a web server listening on the Tor network at an .onion address instead of a standard domain name like .com or .org. All of the traffic to and from a hidden service are end-to-end encrypted through Tor relays – without the need for an SSL certificate.
How is this possible? For a regular, non-Tor web service, an SSL certificate is always needed to facilitate encryption over TLS (Transport Layer Security), whether it is a self-signed certificate, or a trusted certificate from a certificate authority. With Tor, all traffic to hidden services are already encrypted by default. Whoever controls the private key corresponding to the .onion address can serve up a hidden service using that identity.
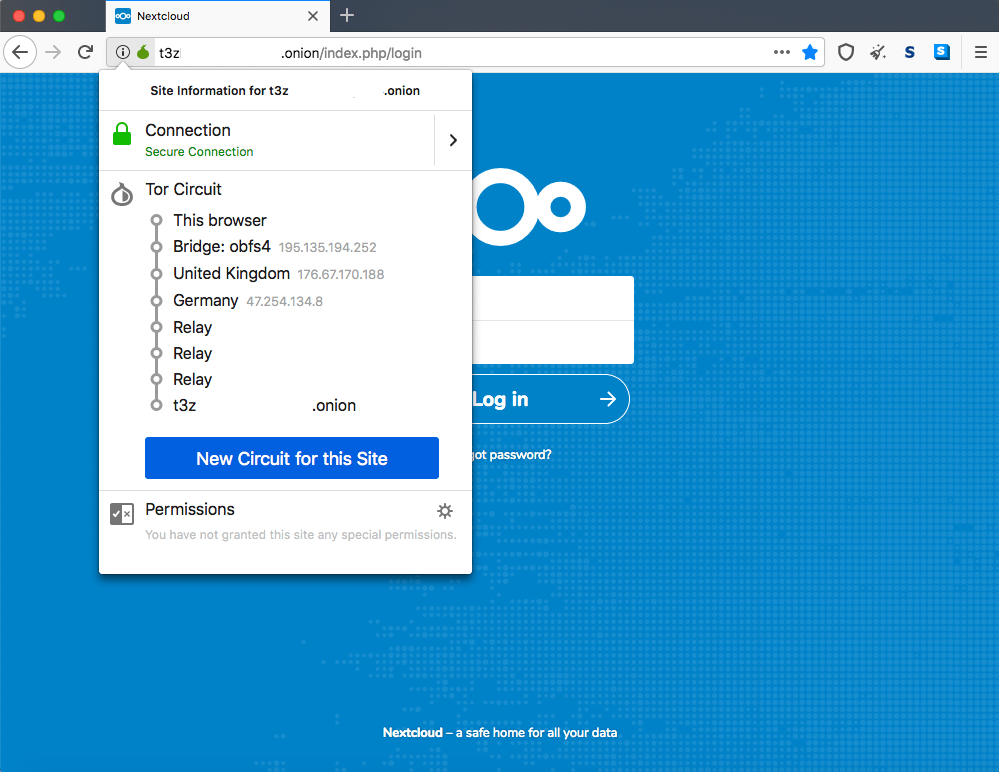
Accessing a Tor hidden service should never be confused with browsing clear web services using Tor. If you use Tor to access an .onion address, the data you transmit is encrypted through to the hidden service hosted at that address. On the other hand, if you access a regular HTTP/S website, the data must past through a Tor exit node, a volunteer operated machine that exits traffic from the Tor network to the clear web. An unscrupulous exit node can trivially intercept all of the non-encrypted traffic passing through it. For this reason, you should always use HTTPS (i.e. encrypted) websites only when browsing the clear web using Tor.
So why would one use a Tor hidden service to host NextCloud? First, Tor is an alternative way of providing encryption to a NextCloud instance besides the usual method with an SSL certificate. Second, Tor has privacy and anonymity benefits beyond what a regular HTTPS page can provide, particularly for circumventing censorship. For example, a journalist or lawyer could use NextCloud on Tor as a “secure drop box” to share files with anybody who needs to mask their IP address from their ISP, government, or other prying eyes.
The example setup in this article should not be taken as a secure setup that is ready for use in the real-world. The setup script uses an older version of NextCloud, and it’s not configured to listen on both the Tor network and the clear web – which may be desirable for some use cases. It is a proof of concept to demonstrate how NextCloud can be hosted as a Tor hidden service, but is not hardened for any critical use. For a custom setup of NextCloud, contact our team for paid consulting.
The NextCloud Onion installer is developed by Centro de Autonomia Digital in Ecuador. It leverages the NextCloud Snap installation method which is optimized for Debian (or Debian based such as Ubuntu) operating systems. The Snap automatically deploys the Apache, MySQL, PHP-FPM, and Redis services on a single machine, and the Onion installer sets up Tor, generates an .onion address, and adds the .onion address as a trusted domain in the NextCloud configuration.
With the Snap, some values such as the memory limit and maximum upload size have already been tuned to 512 MB and 16 GB respectively. The directories where the NextCloud app, data, and config files are stored are documented here.
To deploy NextCloud as an .onion hidden service, simply spin up a new virtual server in the cloud provider of your choice, update the server, and run the NextCloud Onion installer. It’s important to note that the data you store in the NextCloud instance is only as secure as the provider where you choose to host it. We assume you are not trying to do anything illegal (or immoral) but depending on the adversary and threat model, it may be wise to use a server outside of your own country – especially if you might face political persecution. For example, if you use a server owned and operated by a provider in Switzerland, nobody can access the data unless they have a valid court order issued by a Swiss court.
Hosting the .onion hidden service “on premise” at your home or office to protect the physical access to its hard drives may be also a logical choice, as long as using Tor is legal in your country – like in most Western democracies.
In any circumstance, the usual security protocols related to maintaining a web server should be observed. For example, using SSH key authentication only, and updating the apt packages regularly to patch any security vulnerabilities.
We tested the NextCloud Onion installer on Ubuntu 18.04 x64 with a major cloud provider and it worked well. Once the script completes running, the output should look similar to below.
====================== snapd is installed ====================== Installing snap package nextcloud... 2020-01-29T01:00:48Z INFO Waiting for restart... nextcloud 16.0.7snap2 from Nextcloud✓ installed Please input the next values in order to configure the NextCloud admin account: Username: onion Password: Password (again): ====================================================== Username:onion Password: REDACTED ====================================================== Applying credentials values to NextCloud admin account... Nextcloud was successfully installed Configuring NextCloud, please wait... Configuring hidden service... \tBacking up original torrc configuration... '/etc/tor/torrc' -> '/etc/tor/torrc.orig' Restarting Tor service... \tTor onion service file does not exist yet [1 / 20] Onion HiddenService: REDACTED.onion System config value trusted_domains => 2 set to string REDACTED.onion The Hidden Service address has been added like trusted domain succesfully. The Onion Hidden Service address was copied to your clipboard. http://REDACTED.onion Paste the address in your Tor browser.
Fire up a copy of the Tor Browser and copy and paste the .onion address outputted by the NextCloud Onion installer into the address bar. You can login with the admin username and password that you specified when prompted by the installer script.
 To configure the NextCloud desktop client to sync with the NextCloud Tor hidden service, switch to the Network tab and configure a SOCKS5 proxy with address 127.0.0.1 and port 9150. Note that Tor Browser must always be open while you use the NextCloud sync client, because the Tor daemon only runs into the background when the browser is running. If you wanted, you could configure a standalone Tor daemon separate from Tor Browser.
To configure the NextCloud desktop client to sync with the NextCloud Tor hidden service, switch to the Network tab and configure a SOCKS5 proxy with address 127.0.0.1 and port 9150. Note that Tor Browser must always be open while you use the NextCloud sync client, because the Tor daemon only runs into the background when the browser is running. If you wanted, you could configure a standalone Tor daemon separate from Tor Browser.
 Also, configuring the Tor proxy for the NextCloud desktop client means that all NextCloud accounts signed in on the same client will sync over Tor, even for other instances that may be hosted on a regular HTTPS server. This may not necessarily be desirable, as the sync speeds are much slower with Tor.
Also, configuring the Tor proxy for the NextCloud desktop client means that all NextCloud accounts signed in on the same client will sync over Tor, even for other instances that may be hosted on a regular HTTPS server. This may not necessarily be desirable, as the sync speeds are much slower with Tor.
Then, add a new sync account. When prompted, select “Log in” (instead of “Register with a provider”). Enter the .onion address beginning with http:// for the server URL.
A new window will pop-up in your default browser (may not be Tor browser) to authenticate to your NextCloud account. Copy & paste that authentication URL (without www.) into Tor Browser. Because the NextCloud Onion installer does not configure www. as an authorized domain, including www. will result in an untrusted domain error.
Configuring the NextCloud client app on Android to access your NextCloud instance app that is a Tor hidden service is also possible. You will need the Orbot app from the Play Store or F-Droid to proxy the requests from the NextCloud app through the Tor network to access the .onion service.
At this time, accessing NextCloud instances hosted on .onion services through an iOS device is not possible because Apple has not decided to allow Tor or Tor-related apps into their App Store.
We hope this overview has been helpful for assessing the benefits & drawbacks of setting up NextCloud as a Tor hidden service, and that the screenshots above are illustrative how the setup process looks like from both the server and client side. For more information about deploying NextCloud with high performance & security, contact our NextCloud consultants.

