Two factor authentication, or 2FA for short, is a standard security practice that most web-based services that rely on user logins have adopted to reduce the risks arising from password reuse and data breaches across the Internet. Mautic doesn’t have a 2FA feature out of the box, but using either SAML/SSO integration or a Google Authenticator plugin, you can beef up the security of the Mautic dashboard with device-based two factor authentication.
This provides an additional layer of protection if some of the users of Mautic within your organization inadvertently let their passwords fall into the wrong hands.
There could be a lot at stake if the contact data stored within your Mautic instance are accessed by unauthorized third-parties, especially in light of regulations such as the GDPR. The GDPR requires organizations to take “appropriate technical and organisational measures” to safeguard the personal data of EU data subjects. Enabling 2FA in Mautic could be considered one of such technical measures. Also, consider that a personal data breach could adversely impact the reputation of your company, since the GDPR requires the data controller to notify the “proper supervisory authority” and the data subject themselves of any “unauthorized disclosure of, or access to” their personal data “without undue delay.” The personal data breach disclosure requirement particularly applies if sensitive personal data was breached in an unencrypted, or unsalted and hashed format.
Taking some proactive security steps, such as enabling 2 factor authentication, allows your organization to minimize the risk of data breaches and the potential embarassment of notifying your prospects and customers that their data has been breached.
One of the methods of enabling 2 Factor Authentication for Mautic relies on an identity provider (IDP) service called SAASPASS. It takes advantage of the SAML/SSO integration in Mautic (Settings > Configuration > User/Authentication Settings) where an IDP file is uploaded to redirect from the Mautic login page to a SAML login page hosted by SAASPASS. From the SAML login page, marketing users can login to Mautic with one tap from the SAASPASS mobile app (protected by PIN or fingerprint), scanning a QR code using their iOS or Android device, or even by proximity with Bluetooth technology. For up to 10 users, the price is $10/month. Although SAASPASS supports auto-provisioning logins from their Active Directory and LDAP integration for hundreds of other apps, for Mautic, the matching user accounts must still be manually provisioned by a Mautic administrator from the Settings > Users dashboard.
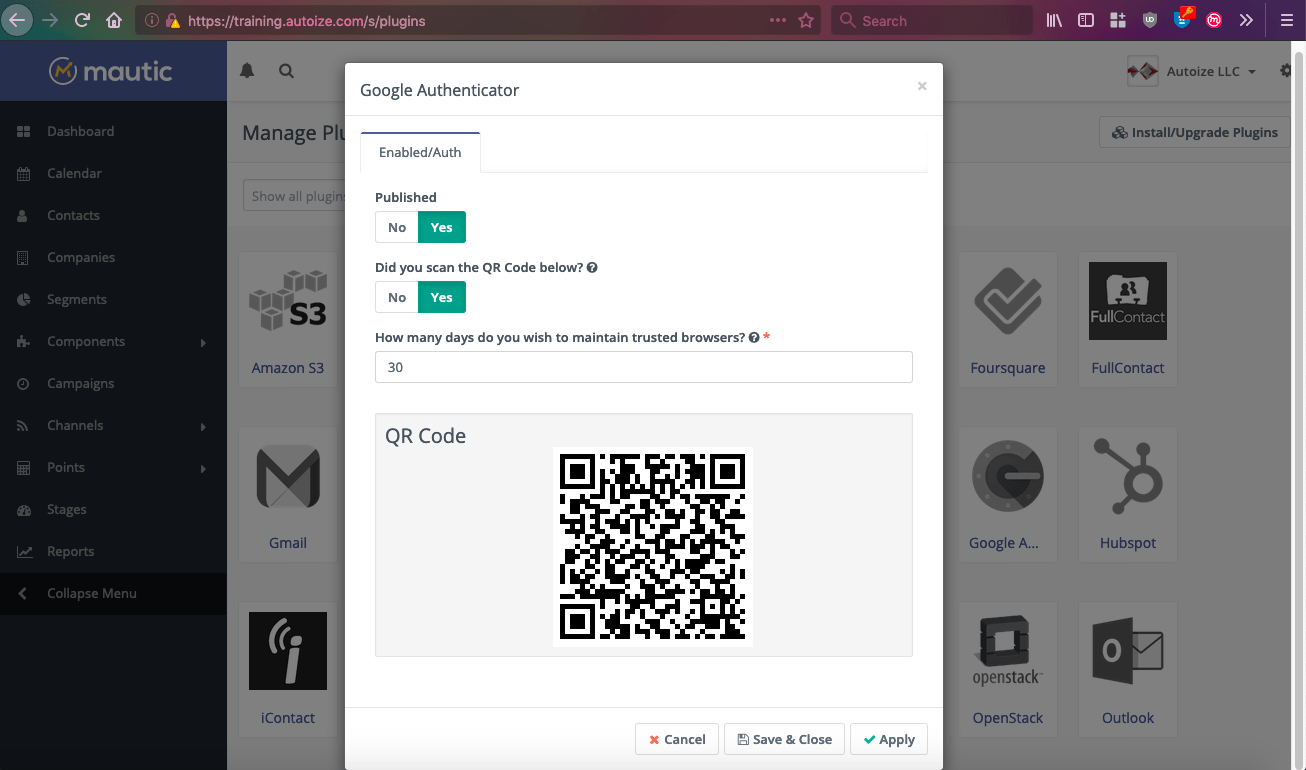
 The other option for enabling 2 Factor Authentication for Mautic is by using the open source Mautic Google Authenticator plugin. This option requires no monthly fee and can be used with any authenticator app (e.g. Google Authenticator, Authy) or password manager (e.g. 1Password, LastPass) supporting TOTP OTP (time-based one-time password) tokens. We tested the plugin with Mautic 2.15.3, the latest version of Mautic at the time of this writing, and it works flawlessly. Installing the Google Authenticator plugin follows the same process as any other Mautic plugin. You should download the release .zip file from the Github page, extract it to the plugins directory of the Mautic installation you wish to protect, and clear the Symfony cache. Then go to Settings > Plugins in the Mautic dashboard and click Install/Upgrade Plugins. Once the Google Authenticator plugin shows up in the list of plugin icons, any Mautic user (including non-administrators) can login to enable the plugin for their account, and scan their unique QR code to generate TOTP tokens – which will be required at login. The number of days that a “trusted device” should be remembered, and therefore not prompted for two factor authenitcation, can also be configured from the same screen where the Google Authenticator plugin for Mautic is enabled.
The other option for enabling 2 Factor Authentication for Mautic is by using the open source Mautic Google Authenticator plugin. This option requires no monthly fee and can be used with any authenticator app (e.g. Google Authenticator, Authy) or password manager (e.g. 1Password, LastPass) supporting TOTP OTP (time-based one-time password) tokens. We tested the plugin with Mautic 2.15.3, the latest version of Mautic at the time of this writing, and it works flawlessly. Installing the Google Authenticator plugin follows the same process as any other Mautic plugin. You should download the release .zip file from the Github page, extract it to the plugins directory of the Mautic installation you wish to protect, and clear the Symfony cache. Then go to Settings > Plugins in the Mautic dashboard and click Install/Upgrade Plugins. Once the Google Authenticator plugin shows up in the list of plugin icons, any Mautic user (including non-administrators) can login to enable the plugin for their account, and scan their unique QR code to generate TOTP tokens – which will be required at login. The number of days that a “trusted device” should be remembered, and therefore not prompted for two factor authenitcation, can also be configured from the same screen where the Google Authenticator plugin for Mautic is enabled.
 We can add two factor authentication to your existing Mautic instance, or set up a new Mautic instance with two factor authentication using a SAML/SSO login page, or TOTP one-time password authentication. Contact us about Mautic 2FA options and other security measures (e.g. kernel-level disk and database encryption) to protect your marketing database from hackers, who could include unscrupulous competitors or cybercriminals running spear-phishing campaigns against your customers.
We can add two factor authentication to your existing Mautic instance, or set up a new Mautic instance with two factor authentication using a SAML/SSO login page, or TOTP one-time password authentication. Contact us about Mautic 2FA options and other security measures (e.g. kernel-level disk and database encryption) to protect your marketing database from hackers, who could include unscrupulous competitors or cybercriminals running spear-phishing campaigns against your customers.

